Definition
With the evolution of technology and its new functionalities, along with new vulnerabilities, new technical tasks have appeared which must be worked on day by day to continue improving. With this evolution, new jobs have appeared to improve the functioning of companies. Today we want to talk to you about the figure of the CISO within a company.
Every company that works with an IT part will need the figure of the CISO in their organization. To understand the functions, your day to day, the problems and mistakes you should never make; it is necessary to understand and define what a CISO is.
We have resorted to the Tech Target definition which says: the Chief Information Security Officer (CISO) is a high-level executive responsible for developing and implementing an information security program, including procedures and policies designed to protect company communications, systems, and assets from internal and external threats. The CISO may also work with the CIO or CIO to purchase cybersecurity products and services and manage the Disaster recovery and the business continuity plans.
To also understand what decision-making power a CISO has, it is important to see the usual schedule in an organization. This will vary according to the scale of the company and its needs. The CISO has an executive role and works under the command of the CSO (Chief Security Officer), at the same time, it informs the CEO (Chief Executive Officer) for taking decisions. Everything and the existence of this schedule the figure of the CISO, in recent years, is gaining weight in business decisions. The path it is taking is logical, seeing the importance that cybersecurity has taken within digital transformation strategies.
Functions
The main function of the CISO should be to improve the IT security system, closely following the improvement and evolution steps of the company. At the same time, to grow in accordance with the organization, you must understand the objectives and needs of the company and adapt the security to it so that it can improve with security and stability. This achieves a lower risk of escape or attack. The changes or advances will come in measure of the technical, human and economic possibilities of the company.
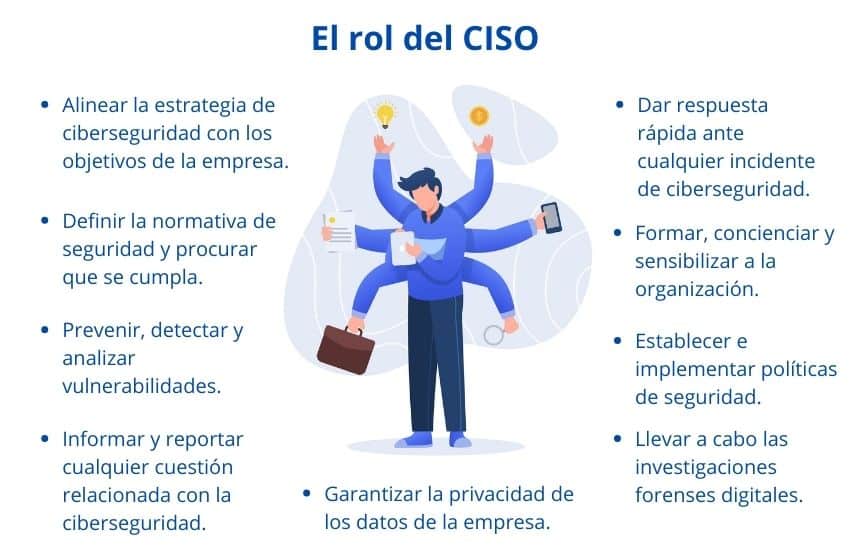
Thus, the specific functions of a CISO according to IEBS are:
- Align the cybersecurity strategy with the company's objectives.
- Define safety regulations and ensure compliance.
- Prevent, detect and analyze vulnerabilities.
- Inform and report to management any issue related to cybersecurity.
- Provide a quick response to any cybersecurity incident.
- Train, educate and sensitize the organization in matters of information security.
- Establish and implement policies related to company security.
- Guarantee the privacy of company data.
- Conduct electronic discovery and digital forensic investigations.
- Supervise and manage the architecture, security audits and information access control.
At the same time, you must be able to develop and train a team for efficient task transfer. Time is vital for the CISO, in cybersecurity every second counts, that is why a good transfer of tasks will give more freedom to focus on priority tasks.
Another function, although sometimes not considered as such, is that of convince the relevant company of the need to invest in security on an ongoing basis. This investment is of time and money but it is necessary for a safe long-term evolution. There are many experts who think that there are only two types of companies: 'those who have already been attacked and know it and those who have been attacked and don't know it'. For CISOs, the reluctance in many companies to invest in cybersecurity is a problem. That's why CISOs should focus their attention on raising awareness since there are still many of these organizations that begin to act when it is too late. Act when they have suffered a theft, disappearance of data, detection of suspicious activities, exit of confidential documents or others, it no longer works, the damage is done. Here lies the importance of awareness.
It will also be important to make companies aware that resorting to cybersecurity only when they have problems with their data or want to comply with what the law establishes is not the solution. Companies solve the problem and do not delve into their security to improve it.
'The 66% of the Cisos around the globe estimate that their organization is not prepared to face a cyber attack today, a 53% in Spain', according to the Voice of the Ciso study, prepared by Proofpoint
Tasks of a CISO
The tasks that the CISO must perform are very extensive and important and he cannot spend all day reviewing small details and generating reports. These tasks are very important, but these processes can be carried out in an automated way or by the team. Hence the importance of a good team. In cybersecurity, no element can stand still and they are all necessary.
The fixed daily tasks that a CISO should perform are:
- Meet with your team. It doesn't have to be a physical meeting and it doesn't have to be a long meeting. This meeting is a first contact every morning to see what projects are underway, functions are assigned and daily tasks are assigned, with their respective deadlines.
- Manage email. This management must be daily and the objective is to achieve a zero inbox.
- Recognize a job well done. It is an important task to keep the team motivated and united so that they feel recognized and valued.
- Spend some time working alone. In the day to day of the CISOs, not everything should be meetings. Time alone is also necessary to analyze, think, review, define strategies, etc.
- Keep up to date with relationships with customers and suppliers. Although it may not seem entirely necessary, it would be important that, at a minimum, you know the clients you are working with and their needs. In order to be able to create or start projects at the scale or to the needs of the clients.
CISOs in their daily tasks have come to think of the following paradigm where put in the center prevention to daily detection and response.
bugs and problems
In the CISO position, any mistake can become a disaster for the company. That is why you must be prepared for any situation, planning ahead and acting appropriately.
The people of CSO Spain made a document with the 'Key mistakes that take their toll on the CISO' where they show us the 5 most common errors that must be taken into account. Among these we find:
- Fail to prevent a data breach. In the era where digitization is advancing by leaps and bounds, data has become the most precious asset of any company. It will be important to protect them and be aware of their importance as it can seriously affect your reputation.
- Take responsibility for the risks and not communicate them. CISOs who take full company responsibility for risky decisions put their jobs in jeopardy. Consider what the company will and will not tolerate from a security, risk, and compliance standpoint.
- Inability to achieve or maintain compliance. CISOs must be able to comply with regional and national laws such as the GDPR or the LOPD. Work must be done with all departments so that no one fails to comply.
- Unprofessional conduct. Of the CISO and its workers. Failure to correct or remedy inappropriate behavior, such as harassment, can result in the CISO being fired. Unprofessional behavior can also be actions such as tweeting or expressing questionable opinions on a social network.
- Inability to provide reliability and availability. When there is a computer problem, many times the company, or part of it, must be stopped, generating not only economic losses but also temporary ones and, nowadays, time is money. If a CISO is not capable of prevention or, in a worse case, recovery of the damaged parts, there could be problems.
Another problem that CISOs encounter is the tendency of the BYOD (Bring Your Own Device). With this new modus operandi many weaknesses are created because own devices are used simultaneously for work and everyday life. Devices must be protected and it is the CISO's job to educate employees and protect their work devices and, consequently, take care of the company. The organization must also be in charge of providing protection systems such as antivirus for all devices or providing directly protected software.
The Shadow IT, also related to BYOD, it also raises fear. Shadow IT is any computer device, software or service, generally cloud-based, that is used in an organization but is outside the control of the organization's IT department or is used without its knowledge or approval. The CISO is in charge of to protect without hindering the day-to-day activities of employees and offer tools that the business also approves. The use of third-party sharing tools such as email also It gives headaches since, although it is very useful for messaging, it does not have the necessary protection for organizations.
According to Microsoft, 90% cyberattacks start with an email.
The human error It can also become a serious problem within an organization due to deliberate data leakage, clicking on malicious links (via email or web), downloading compromised files, weak passwords, among others. These actions put companies at risk on a daily basis.
According to ICT Director 68 % of CISOs in Spain continue to consider human error as the greatest cybersecurity vulnerability in their organization.
Recommendations for CISOs
From ComputerWorld they affirm: the recommendations that can be made to each and every one of the companies is that they dedicate a part of the annual budget to cover the cybersecurity needs of the company, that they make all staff aware of the associated risks and train them periodically on these issues, that have and/or design Security Master Plans and that have their own or subcontracted personnel qualified for cybersecurity matters to whom they can consult / resort if necessary.
According to a survey conducted by consulting firm Ernst and Young, 87% of participating organizations said they did not have enough budget to achieve the levels of cybersecurity and resiliency they were seeking. A lack of resources means companies can't hire enough cybersecurity talent or put in place the technical measures they need to counter attacks.
More and more CISOs are betting on hiring a cyber insurance. These serve for 'after attack' protection. They help organizations, not only with financial remuneration, but also, in case of robbery or extortion, in negotiation.
Byte It gives us 4 recommendations for CISOs:
1. Prioritize risk.
2. Plan cybersecurity tools.
3. Strengthen the basic points.
4. Get tools and capabilities at the right scale.
The recommendation of Alex Manea (BlackBerry) is: “My advice to CIOs and CISOs is to think like a hacker”
There are already many CISOs who rely on external tools to increase the protection of their company.
transfer is the preferred tool for CISOs to fight against Shadow IT and reinforce their security director plan for file sharing, avoiding GDPR sanctions and information leaks through qcloud tools:
- Send and receive files securely
- Choose your shipping preferences and
- Display
- Prevents entry and exit of Malware
- Control information leakage
- End-to-End Encryption

More than 1 million licensed users
More than 5 million recipients
Contact us for more information: [email protected]
Or through our social networks:
Sources:
https://cso.computerworld.es/alertas/errores-clave-que-pasan-factura-al-ciso
https://cso.computerworld.es/pubs/cso21/index.html?page=40
https://red.computerworld.es/actualidad/que-hace-un-ciso-en-su-dia-a-dia
https://cso.computerworld.es/tendencias/el-ciso-cada-vez-mas-presente-en-las-decisiones-de-negocio
https://searchdatacenter.techtarget.com/es/definicion/CISO-director-de-seguridad-de-la-informacion
https://www.audea.com/la-figura-del-ciso-funciones-e-importancia/
https://arandasoft.com/tareas-que-un-cio-debe-cumplir-todos-los-dias/