Red Team, Blue Team & Purple Team. Action, Advocacy and Evaluation
The cybersecurity sector is constantly evolving and it is necessary to be prepared for each of the possible situations that may occur. That's why they exist different cybersecurity teams: the Blue Team, the Red Team and the Purple Team. Each one has a different function and are used to Evaluate and analyze possible failures in the system.
The terms RedTeam Y BlueTeam are commonly used to describe teams that use their abilities to evaluate a company's cyber defense. O well imitate the attack techniques that the “enemies” could use (red team), either the teams that use their abilities to defend (Blue team). In fact, these teams play an important role in defending against advanced cyberattacks that threaten business communications, sensitive customer data, or trade secrets.
When we talk about computer security and data protection, these two teams are essential. Thanks to the fact that they carry out complementary work to detect vulnerabilities, prevent computer attacks and emulate threat scenarios.
To understand in detail the operation and functions of each piece of equipment, we will describe each one:
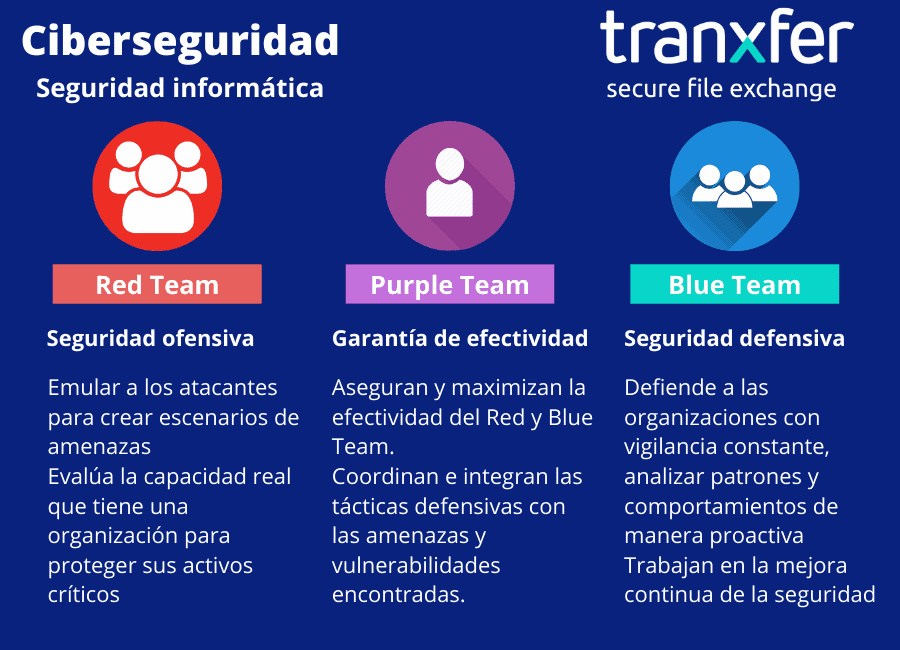
RedTeam
The Red Team is the one we named offensive security and is made up of security professionals who They act as adversaries to get past cybersecurity controls. He is in charge of testing the Blue Team looking for vulnerabilities.
The Red Team radically attacks the system to test the effectiveness of the security program. This attack is not warned so that the defense is with maximum objectivity and see what a real attack would be like. The attacks carried out can be internal to the company itself or it can be from an external company. Teams are typically made up of ethical hackers who assess security objectively.
It is often confused with the figure of pentesters since there is some overlap between their functions and abilities, but they are not the same. The pentesters carry out an intrusion process with pivoting techniques, social engineering and other hacking tests that end with a report in which vulnerabilities are identified.
With the creation of the different attacks, it is possible to see the possible security leaks and to see the behaviors and possible techniques of future attackers. The effectiveness of the Red Team lies in constantly checking the possibility that someone external to the company could have access to the systems and could modify them.
How does a Red Team work?
The Red Team, although it may not seem like it, spend more time planning an attack than carrying out attacks. In fact, the Red Team is responsible for implementing a series of methods to gain access to a network. The Red Team is hired to test the effectiveness of the blue team by emulating the behavior of a real black team (cyber attackers) so that the attack is as realistic and chaotic as possible.
They use a wide variety of methods and tools to exploit and bring down weaknesses and vulnerabilities in a network.. Among those we could find phishing, identification of vulnerabilities, firewall intrusion, etc. It is important to note that these teams will use any means necessary, under the terms of the engagement, to break into a system. Depending on the vulnerability, they can deploy malware to infect hosts or even bypass physical security controls by cloning access cards.
Red Team functions
- The Red Teams emulate attackers, using the same or similar tools. With the attacks they want to exploit security vulnerabilities in systems and/or applications (exploits), pivoting techniques (jump from one machine to another) and objectives (systems and/or applications) of the organization.
- They make a threat scenario emulation process which an organization faces. They do it analyzing security from the attackers' point of view, to give the security team (Blue Team) the possibility of defending itself against attacks in a controlled and constructive way.
- Therefore the Red Team is an entertainment for the Blue Team, where evaluates the real capacity that an organization has to protect its critical assets and its detection and response capabilities considering both the technological, process and human aspects.
BlueTeam
The Blue Team is the one we named defensive security and is made up of security professionals who are responsible for protecting critical assets of the organization against any threat. It is responsible for proactively defending real and programmed attacks by the Red Team.
Everything and that conventional cybersecurity teams have tareas similar differs from the Blue Team. This has the functionality of constantly collecting surveillance data for continuous evaluation, while conventional cybersecurity teams only act when receiving attack input. He Blue Team is usually made up of internal staff cybersecurity of the organization.
The Blue Team aims to analyze patterns and behaviors that are out of the ordinary. It is also responsible for making evaluations of the different threats that can affect the organization, monitor and recommend action plans to mitigate potential risks. To prevent attacks, they create a database with a range of possible use cases.
In the event of an attack, the Blue Team takes action and performs response tasks, including forensic analysis of the affected machines, traceability of the attack vectors, proposal of a solution and establishment of detection measures. Although the Blue Team is usually used to defend against large attacks, it evaluates and analyzes any security flaw that happens in the system, even if it is tiny.
How does a Blue Team work?
The Blue Team starts with a first data collection, document exactly what needs to be protected and carry out a Risks evaluation. They then enforce access to the system in many ways. They also take care of the staff education on security policies such as stronger passwords and make sure they understand and adhere to security procedures.
Monitoring tools are typically implemented that allow information about system access to be recorded and verified for unusual activity. The Blue Team hacen Periodic checks on the system, such as DNS audits, internal network vulnerability scanning, orand third parties and capture sample network traffic for analysis.
Blue Team Functions
- They make a constant vigilance, analyzing patterns and behaviors that are out of the ordinary both at the level of systems and applications as well as people, in relation to information security.
- They work on the continuous improvement of security, tracking cybersecurity incidents, analyzing systems and applications to identify failures and/or vulnerabilities and verifying the effectiveness of the organization's security measures.
¿How do the red and blue teams work together?

The communication between the two teams is the most important factor for successful exercise and for constant improvement of the system.
The Blue Team must keep up to date on new technologies to improve security and must share all information with the Red Team in order to carry out test attacks. Likewise, the red team must always be aware of new threats and penetration techniques used by hackers and advise the blue team on prevention techniques.
Depending on the objective of your test, the Red Team will or will not inform the Blue Team of a planned test. For example, if the goal of the attack is to simulate a real response scenario, Blue Team will not be notified about the test. Only someone in management needs to be informed about the test for further analysis, usually a Blue Team leader.
When the test is complete, both teams collect information and report their results. The Red Team warns the Blue Team if they manage to penetrate the defenses and provides advice on how to block attempts similar to a real scenario. In the same way, the Blue Team informs the Red Team whether or not their monitoring procedures detected an attempted attack.
Ultimately, both teams must work together to plan, develop and implement security controls more stringent as needed.
Purple Team
The Purple Team exists to analyze and maximize the effectiveness of the Red and Blue Team.
This team is in charge of confronting the defense techniques of the Blue Team against the attack techniques of the Red Team. With this confrontation it is possible to create more possible cases of failure or attack and to see if the system is working and is prepared correctly. If the defense in the confrontation is positive, the new scales or pertinent updates are integrated.
The idea of the Purple Team is coordinate and ensure that the two previous teams share information about system vulnerabilities. With the objective of achieve constant improvement, the Purple Team is more than a team, it is a coordinator of the Blue and Red Team.
The Purple Team coordinates the Red and Blue Team to guarantee its correct functioning and evolution
Functions of the Purple Team
The main objective of the Purple Team is manage the security of the organization. They do itperformdo testing to verify the effectiveness of security mechanisms and procedures and define/develop additional security controls to reduce organizational risk.
For both companies and institutions, it is essential to implement security controls to minimize the risks of a cyber attack and protect the data they handle.
What advantages does the existence of these teams have?
- They strengthen your entire system. With the test and creation of security by Blue Team, your system will be strengthened and new, more effective security measures will be created.
- Creation of action plan. With the actions of the Purple Team you will be able to create different action plans. You will be able to foresee possible attacks or other computer problems found by Red Team attacks.
- Tranquility. With the attacks and defenses of the Blue and Red Team, although it can always be improved, you will know that your system is protected.
Although the different cybersecurity teams help to create a good defense against possible attacks, we must not forget that cyber attackers are constantly training and evolving to find a minimum gap to access. That is why it is vital to be continuously analyzing all security systems. AND more nowadays, where cyber attacks on companies do not stop increasing.
"Cyberattacks in Spain have grown by 125% in the last year to 40,000 daily"
Source: CyberSecurity News – 2021
This increase in cyberattacks is caused by the rapid introduction to the digital world of many companies that have been forced to make the change due to the pandemic. It has also been caused by the incorporation of teleworking, since many companies were not prepared for this change. That is why the implementation of cybersecurity is so important and vital for companies.
More than 1 million licensed users and more than 5 million receivers
Contact us for more information: [email protected] or through our social networks: LinkedIn either Twitter