Tranxfer and its new functionality, the «Tags»
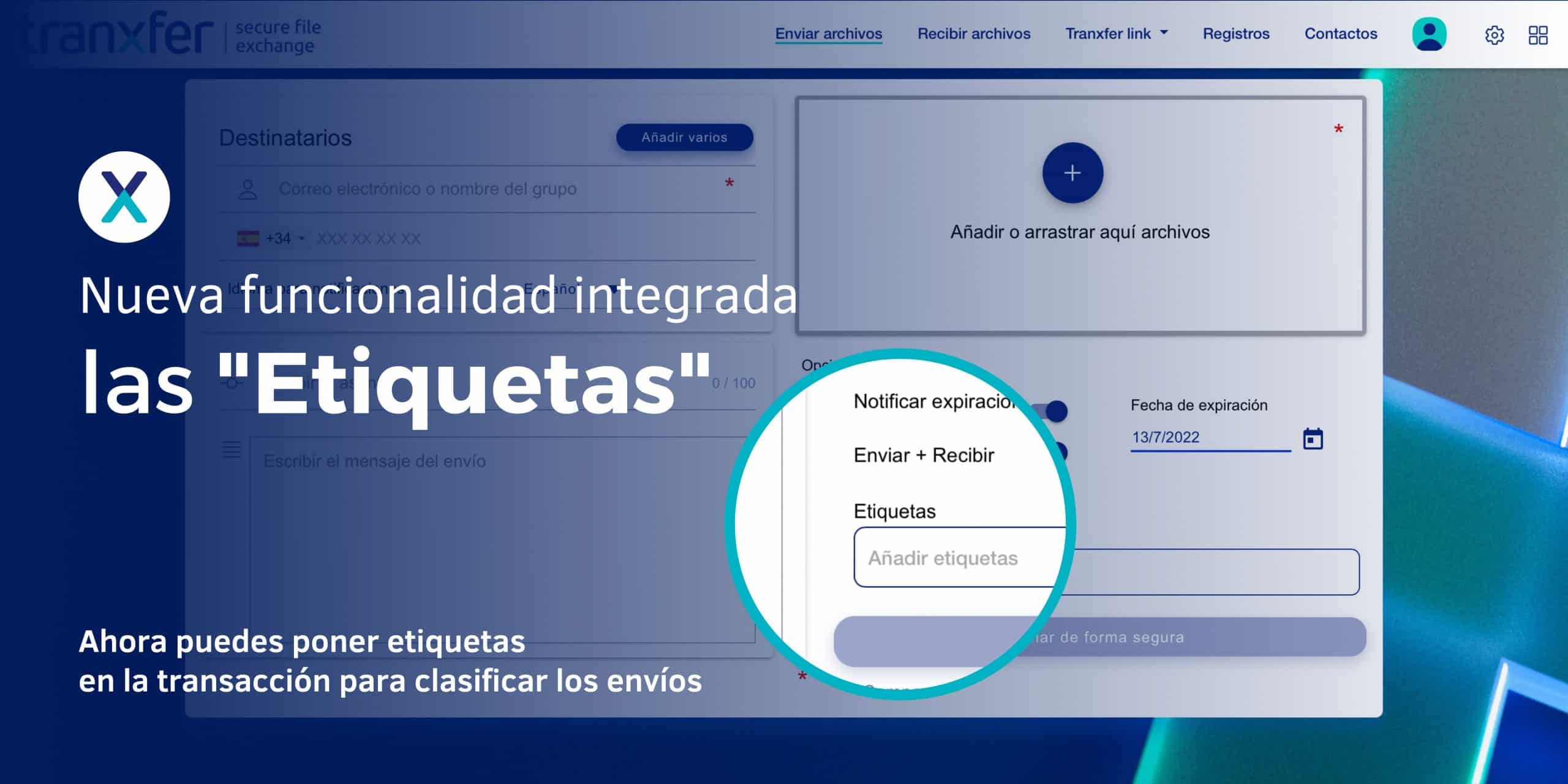
Ahora Tranxfer permite clasificar las transferencias con «Tags» ¿Para qué sirven las etiquetas o «Tags»? Las etiquetas sirven para clasificar. Muchos servicios digitales ofrecen la posibilidad de poder etiquetar los movimientos dentro de su plataforma, para así poder filtrar y encontrar a posteriori las diferentes acciones de una manera más rápida. Las etiquetas són a título individual, y pueden servir para indicar muchas cosas, el tipo de archivo, tamaño, importancia, temática, … y luego desde el panel principal puedes filtrar por aquellos que tengan “X” etiqueta. “Cómo utilizar las etiquetas en Tranxfer” Las etiquetas en Tranxfer, sirven para poder clasificar las transferencias que se hacen usando la plataforma. Puedes etiquetar o bien las transferencias en general, cómo poner etiquetas en los ficheros en sí. Para etiquetar la transferencia dirígete al recuadro inferior que encontrarás justo al final del interfaz de usuario, inmediatamente antes del botón de “Envío de forma segura”. Pulsa con el ratón sobre el recuadro de “Añadir etiquetas” y a continuación escribe el texto de la etiqueta de la transferencia, puedes usar espacios. Una vez hayas finalizado recuerda pulsar la tecla Intro para completar la creación de la etiqueta. Estará creada correctamente cuando visualices el texto de la misma dentro de una etiqueta gris con una aspa (x). Puedes crear tantas etiquetas como requieras siguiendo estos pasos, y podrás eliminarlas sencillamente pulsando en el aspa (x). Repite este proceso tantas veces como necesites. Para añadir etiquetas a los ficheros que forman parte de la transferencia, primero deberás adjuntar al menos un archivo. Una vez se haya completado con éxito la subida del archivo, podrás ver que en la información del detalle desplegado del archivo dispones de un recuadro que permite escribir etiquetas. El funcionamiento del recuadro es idéntico al descrito anteriormente. Para filtrar, hay que hacer clic en “Registros”, ubicado en el menú superior de la plataforma. Saldrán todos los registros de transferencias, y posteriormente hacer clic en Filtros. Se abrirá una pequeña pantalla dónde podrás aplicar filtros por etiquetas, o por fechas. Para buscar una etiqueta recuerda pulsar la tecla Intro igual que para crearlas, cuando visualices el texto de la misma dentro de la etiqueta gris con una aspa (x) estará creada correctamente. ¿Cuál es la diferencia entre las etiquetas en la transferencia y las etiquetas en el archivo? Cabe mencionar que ambos tipos de etiquetas tienen el mismo peso y características en la plataforma. La diferencia es que si etiquetas la transferencia en general, cuándo filtres aparecerá la transferencia con sus archivos, en cambio, si etiquetas los archivos, sólo saldrán los archivos individuales. Por ejemplo, si etiquetas una transferencia, cuándo apliques el filtro desde la consola principal, saldrá la transferencia y sus archivos. Si, por otro lado, etiquetas el fichero, solo saldrán los ficheros que tengan esa etiqueta. Mejores prácticas con las Etiquetas Una vez hayas transferido transacciones con etiquetas, podrás acceder a la información en el Detalle de Registros. Localiza la transferencia en cuestión y pulsa en esta para ver los detalles de la misma. Encontrarás toda la información correspondiente a la transferencia así como de los archivos junto las etiquetas que usaste en su momento. Las etiquetas son dinámicas de manera que sigues teniendo opción de añadir nuevas o bien eliminarlas en cualquier momento. Desde la ventana con la vista general de registros puedes aplicar filtros para refinar las transferencias que deseas visualizar por pantalla y obtener aquellas que concuerden con las etiquetas que hayas creado. Pulsa en la opción Filtros con forma de pirámide invertida en la zona superior derecha, y escribe las etiquetas por las que deseas filtrar. Recuerda que la mecánica y uso de Etiquetas en Tranxfer dispone de su versión API para ser aplicada en el desarrollo de aplicaciones y servicios. Aquí puedes ver todas las características de Tranxfer.